The ESET Research Center has detected an unusual phishing campaign targeting mobile phone users and analyzed a phishing incident that targeted customers of a well-known Czech bank.
This method requires caution because it installs the application phishing from a third-party website, without the user giving permission to install third-party applications.
On Android, this can lead to the “silent” installation of a special APK file, which is actually presented as having been installed from Google Play. The campaign also targeted iPhone (iOS) users.
Phishing websites that target iOS software invite victims to add an Progressive Web Application (PWA) on their home screen, while on Android, the PWA is installed after the confirmation of pop-ups in the browser. At this point, on both operating systems, the applications phishing they closely resemble the real banking applications they emulate. PWAs are essentially web pages that look like standalone applications, with that feeling enhanced by the use of system commands. PWAs are cross-platform, which explains how these campaigns target both iOS and Android users. The new technique was spotted in the Czech Republic by ESET researchers working on the ESET Brand Intelligence Service, which monitors threats against a client’s brands.
“For iPhone users, such an action could undermine the sense of the protected environment that the ecosystem provides,” says ESET researcher Jakub Osmani, who analyzed the threat.
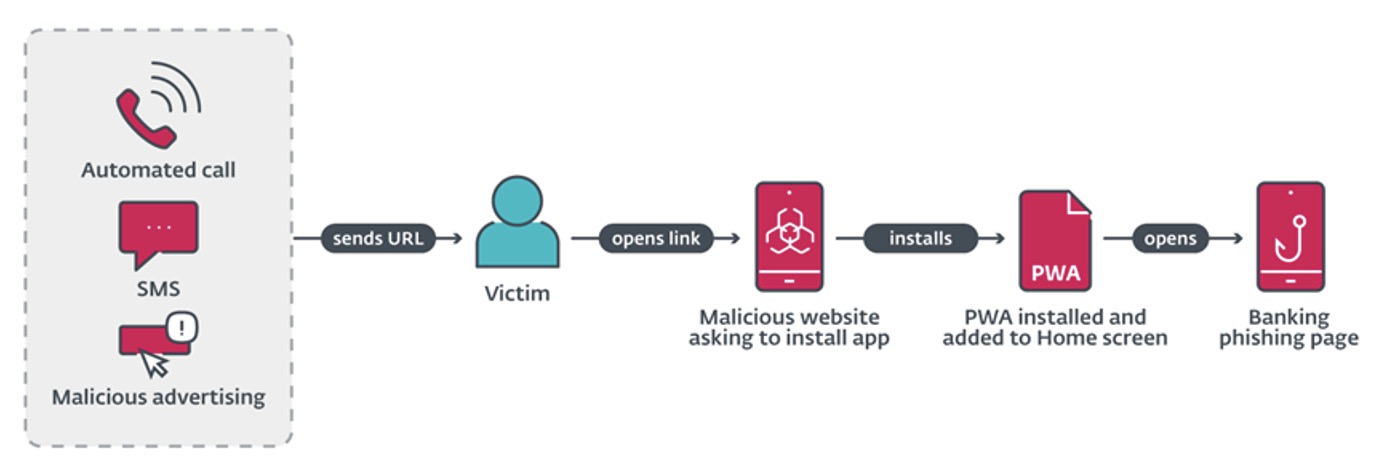
The phishing campaign uncovered by ESET researchers, used three different mechanisms to distribute URLs. These mechanisms include automated voice calls, SMS messages and malicious advertising on social media. In one case the distribution of the URL is via an automated call that alerts the user to a banking application that needs an update and prompts them to press a button on the keyboard. After the correct button is pressed, a phishing URL is sent via SMS.
SMS distribution was carried out by sending messages indiscriminately to phone numbers in the Czech Republic. The message sent included a phishing URL and text to trick victims. The malicious campaign was also spread through advertisements on Meta platforms such as Instagram and Facebook. These ads included some limited offer for users who will “download the following update”.
After opening the URL delivered in the first stage, Android users are directed to either a phishing page that mimics the official Google Play Store page for the particular banking app, or a fake webpage of that app. From here, victims are prompted to install a “new version” of the banking app.
The phishing campaign and method is only possible because of Progressive Web Apps (PWA) technology. In short, these are applications built using traditional web application technologies and can run on multiple platforms and devices. WebAPKs could be considered an upgraded version of Progressive Web Apps (PWAs), as the Chrome browser generates an Android app from a PWA: in other words, an APK. These WebAPKs look like regular apps. Additionally, installing a WebAPK doesn’t trigger any of the “install from an untrusted source” warnings. The application will be installed even if installation from third-party sources is not allowed.
One group used bot of Telegram to record all input information in his group chat Telegram through the official API of the application, while another team used a traditional server Command & Control (C&C) with a management panel. “Based on the fact that the campaigns were using two different infrastructures C&Cwe found that two separate teams were managing the campaigns phishing PWA/WebAPK against the Czech Republic and other banks”, concludes Osmani. Most of the known cases occurred in the Czech Republic, while only two applications phishing appeared outside the country (specifically in Hungary and Georgia).
All sensitive information identified by ESET’s investigation into this matter was immediately sent to the affected banks for processing. ESET also helped take down multiple internet phishing addresses and C&C servers.
For more technical information about the new phishing threat, see the blogpost «Be carefulwhat you pwish for – Phishing in PWA applications» at WeLiveSecurity.com. Make sure you follow her ESET Research on Twitter (now known as X).
